The Leading Graph Database for Cybersecurity
The only open-source, multi-tenant and ultra-fast security graph for CNAPP, CSPM & CIEM that’s ready to scale with you.
- 10K+ Multi-Tenant Graph
- Real-Time Detection
- Cypher support
"Defenders think in lists. Attackers think in graphs. As long as this is true, attackers win.”
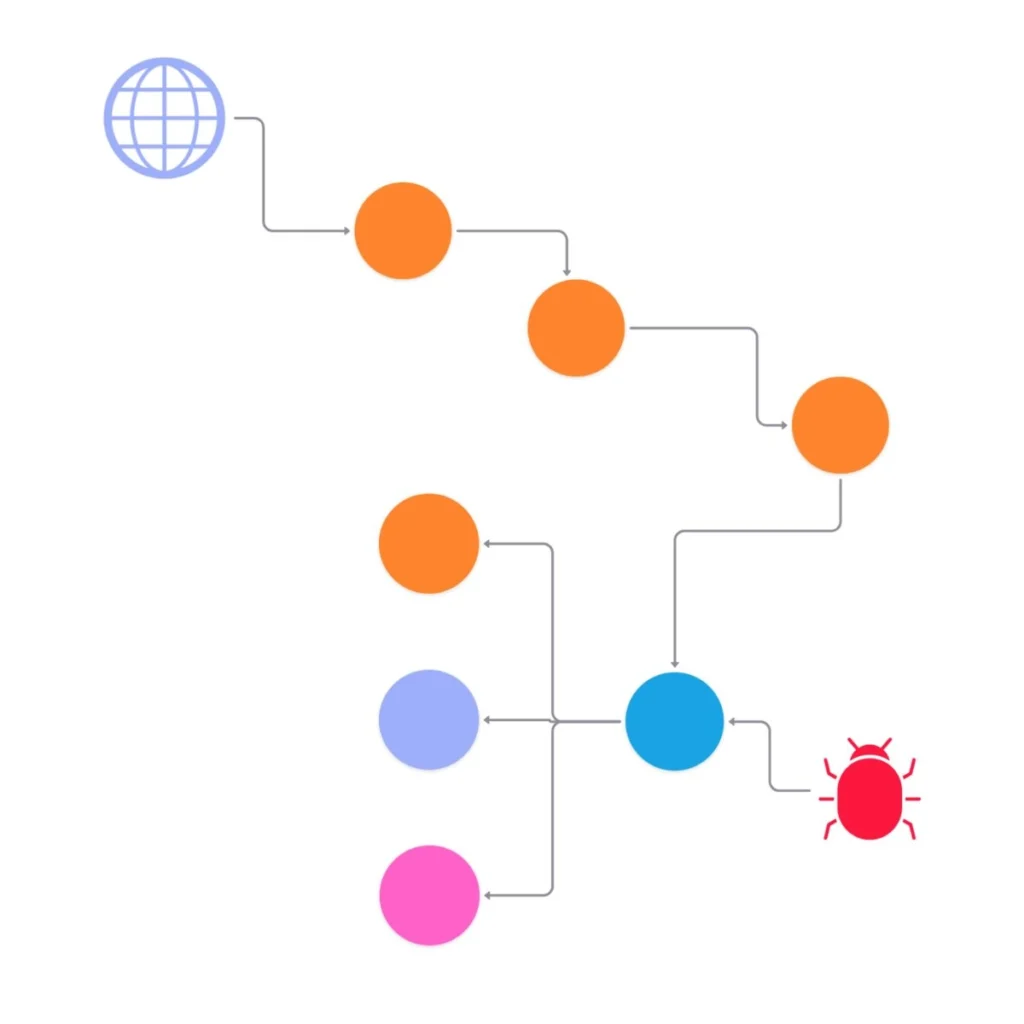
Graph modeling of your cyber data
Your security data is already interconnected, making graph representation ideal for advanced Cypher querying.
Built-in multi-tenancy
Manage 10K+ tenants effortlessly with fully isolated tenant data, zero wasted infrastructure, and out-of-the-box scalability for future workloads.
Real-time detection
Current solutions fail when low latency matters. Process multi-hop graph queries in milliseconds, enabling real-time insights.
Proper user experience
Deliver a frictionless experience as users interact with dashboards, filter data, and build custom views, providing UX that differentiates your product.
6 Reasons you need a graph to store your security data
Security data naturally forms graphs: IP addresses connect to domains, users access systems, and attack patterns propagate through network relationships. Relational schemas force this interconnected data into rigid table structures that resist evolution as threat landscapes change. Graph databases preserve these relationships natively while supporting schema flexibility that scales with your security requirements.
The Challenge
You receive thousands of alerts daily. Prioritization and correlation are impossible without context.
How it affects you
Analysts burn time on low-value triage. Real threats blend in with noise.
Why choose graph
Graphs enable end-to-end context resolution. For example, you can correlate IAM misconfigurations with workload vulnerabilities and data exposure paths.
Business impact
Fix the most important incidents first. Fewer false positives. Higher fidelity threat models.
Ideal for
CNAPP
DAST
CSPM
CIEM
SAST
IAM
Stop firefighting, start preventing.
Your data already forms a graph. We give it structure and speed. The result is faster investigations, smarter risk prioritization, and a simpler path to securing complex cloud infrastructures.
- 10K+ Multi-Tenant Graph
- Real-Time Detection
- Cypher Support